Enforcing Ransomware Platform Protections with the Microsoft Power Platform
Discover how Power BI, Power Automate, and the rest of the gang keep your business safe from ransomware platform attacks
Table of Content
The Microsoft Power Platform allows users to work with data and build custom apps, websites, and automations that protect your organization, surface detailed insights that detect anomalies and threats in real-time, and embed security protections into your creations.
All Power Platform solutions operate on a security model provided by Microsoft Dataverse that protects data privacy and integrity, while at the same time, makes it easy for users to access and share critical information.
Individual users are only able to work with data assets they’re already authorized to use, and built-in security features ensure that your citizen developers aren’t empowering hackers to wage a full scale ransomware platform campaign on your system — or your customers’.
In this piece, we’ll look at how Power BI, Power Automate, and the rest of the gang keep your business safe from ransomware platform attacks.
From a ransomware standpoint, Power BI gives users the granular visibility they need to detect, prevent, and respond to ransomware platform attacks across the entire security estate. It’s embedded with industry-leading security features like data encryption, real-time monitoring, and sensitivity labeling — offering additional protections for valuable data.
Power BI’s new data mart feature allows users to run relational database analytics, build reports and semantic models, and manage end-to-end data ingestion, prep, and SQL exploration.
You can also control data governance with row level security (RLS) and sensitivity labels.
And —you can track data lineage and metadata by integrating data marts with Microsoft Purview. You can also make data available to specific groups and “certify” and promote specific data marts so users can find the trusted insights they need.
You can incorporate Power BI data into existing tools like Outlook, PowerPoint, Teams, and Dynamics 365 and use the same data protections (i.e. sensitivity labels, data lineage and impact analysis) you’ll find inside MS365 across all Power BI dashboards, reports, and dataflows.
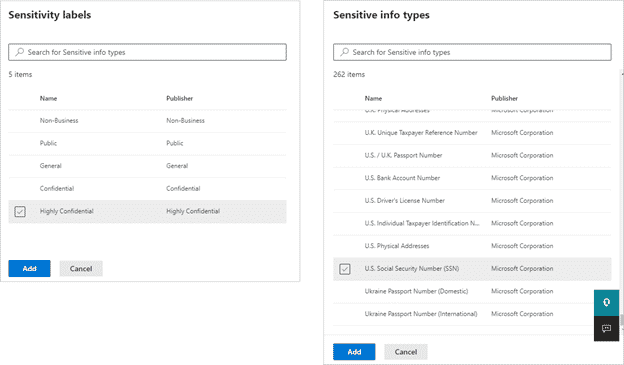
Microsoft also just launched DLP policies for Power BI, which automatically detects sensitive data uploads using the built-in data loss prevention (DLP) policies you’ll find inside SharePoint, Teams, OneDrive, etc.
Low-code development platforms are becoming increasingly essential when it comes to competing amid current conditions – empowering the “citizen developer” to solve problems on their own – with or without any prior coding experience. Of course, these drag-and-drop tools fall apart without built-in guardrails that prevent inexperienced developers from releasing vulnerable apps into the wild.
Here’s a quick look at some of the built-in security protections that Power Apps and Power Pages use to keep ransomware out of custom solutions:
According to Microsoft’s guide to planning a Power Apps project, security protections come into play during the architectural design stage (after you’ve completed the planning phase and come up with a conceptual design).
This is where you’ll figure out how to store your data, what your data structure will look like, and how to integrate the app with existing apps and systems. There are four different security layers you can set up in your app:
Power Pages, just launched in public preview, is a secure low-code website builder you can use to create, publish, and host web portals, external sites, and private intranets.
Like Power Apps, Power Pages has a robust security model in place to protect critical data — though the specific security features are slightly different.
In a recent white paper, Evolving Zero Trust, Microsoft explains that automation plays a central role in protecting your business against ransomware, malware, and other cloud-based threats.
Security solutions with intelligent automation capabilities are helping organizations safeguard critical assets against ransomware platform attacks. It’s becoming impossible for humans to manually patch systems, detect threats, and take proactive action before disaster strikes.
Power Automate users can strengthen their security posture with custom workflows that perform routine tasks like resource provisioning, onboarding, and access reviews.
There’s also the AI Builder, which allows you to build, train, and publish different types of AI models — incorporate them into custom apps. Models can be trained to predict outcomes, classify data, and carry out automated workflows via Power Automate.
So, you might integrate security data from various sources to build a solution that can automatically flag unusual behavior, detect malware, or raise alerts if there’s evidence of fraud. Or – leverage AI and ML to enforce data governance or carry out sequences that prevent, detect, contain, and act on incoming ransomware platform threats.
Power BI unlocks custom insights, providing granular visibility into the security metrics most valuable to you. Power Automate can be used to detect and respond to threats, reinforce policies, and protect data. And – low-code platforms, Power Pages and Power Apps make it easy for your teams to quickly build and deploy solutions without creating an opening for threat actors.
Velosio’s Microsoft experts can help you design and implement focused solutions built on the Power Platform. We’ll help you determine which insights belong in your Power BI dashboards, automate tasks like provisioning or penetration testing, and more.
Contact us today to learn more about our process, solutions, and experience with the Power Platform.
Talk to us about how Velosio can help you realize business value faster with end-to-end solutions and cloud services.
"*" indicates required fields