Guidance for Selecting Anti-Ransomware Tools
Discover key considerations and selection criteria for anti-ransomware tools – so you can lock down your system ASAP.
Table of Content
Keeping up with the tools and solution providers in an ever-expanding and evolving ransomware landscape is, well, a lot for security teams to take on.
While some security pros might enjoy the process of researching and testing new technologies, these employees are already overwhelmed with day-to-day work.
On top of that, implementing the right ransomware stack is a time-sensitive matter.
The more time your team spends evaluating potential solutions, the more opportunities cyber criminals have to exploit vulnerabilities in existing solutions.
In this article, we’ll focus on key considerations and selection criteria for ransomware solutions – so you can lock down your system ASAP.
Defining your requirements is something you should do before researching any potential solution.
It doesn’t matter whether it’s a strategic new hire, a managed services provider, or a few choice investments in your ransomware defense strategy, you need to figure out what you’re looking for before starting your search.
You’ll want to make sure that your ransomware stack addresses the full spectrum of risk vectors — and that it aligns with the specific needs and challenges of your business.
Think — identity and access management, threat intelligence, security automation, and so on — as well as any requirements specific to your industry, business model, or how you run your business.
For example, if you operate in an industry with strict compliance requirements (i.e. financial services, healthcare) or handle a lot of valuable customer data, trade secrets, or IP (i.e. professional services, tech, retail) you’ll want to look for solutions that can help you meet those additional requirements — say, automated data governance or regulatory compliance.
Look at your entire system (we’re talking: performing a full-on audit) and make sure you can answer the following questions:
Here, you’ll want to be as detailed as possible – this will help you limit the number of solutions you test at the same time and ensure that you’re focusing your efforts/resources on relevant solutions.
Next, you’ll want to put together a map of your current digital estate. This includes assets, identities, networks, devices, and any existing security solutions, as well as any gaps or vulnerabilities that need to be addressed.
Aim to uncover blind spots, identify shadow IT and identities, identify risk vectors and data flows.
We recommend using the Zero Trust architecture to help guide this process. The framework is built on the following nine security pillars — all of which will need to be addressed in your stack to effectively defend against ransomware:
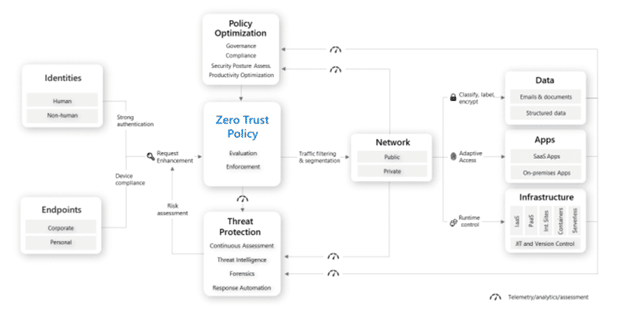
This gives you a starting point you can use to start evaluating solutions that specifically address your security needs.
According to Secureworks, threat actors target gaps between layers – processes, tools, etc. – leaving businesses vulnerable, even after implementing intelligent solutions and robust protections.
Implementing a Zero Trust allows you to systematically seal those gaps and avoid costly breaches or other incidents that could have been prevented. So, ultimately, you’ll want to make sure that your solution(s) covers all of these pillars, plus any unique business requirements that might impact your security posture.
Once you’ve established a set of baseline requirements, you’ll want to use that info to learn what options are out there.
According to Velosio Director of Cloud Carolyn Norton, organizations should, at a minimum, make sure that they’re evaluating solutions and vendors that offer SIEM, XDR, and EDR functionality — and that those core capabilities can be unified in a single pane of glass.
Analyze open source and commercial tools available in the market based on your requirements.
Here are a few examples of questions you might ask to find the best-fit solutions:
You might include additional questions in your evaluation process, depending on what you’re trying to achieve with your anti-ransomware investments.
But – the idea here is to gather enough information to put together a short list of tools you’d like to test before making any big commitments.
Once you’ve narrowed your search, you’ll want to take potential solutions for a test drive before making a final decision.
Keep in mind, you’ll want to follow a systematic testing process, evaluating solutions against the same criteria and under the same conditions. This is super important as it allows you to effectively compare solutions and find the best option(s) for your business needs.
Tools should solve for the specific needs you outlined before getting started. Those might include:
You might consider running a pilot program. Many vendors use proof of concept evaluation criteria to help organizations understand how solutions work in context with a particular industry or use case. But, those are just a starting point – a template that doesn’t include the specific requirements unique to your business. A pilot program allows you to test solutions in a limited capacity – and measure the real impact they have on your business.
You should also set up sandbox environments to learn more about how solutions perform under various conditions.
For example, you might use predictive modeling capabilities to simulate different threat scenarios and evaluate how each solution responds against specific criteria – speed, accuracy, whatever.
Avoid taking a “best-in-breed” approach to security.
See, fragmentation slows you down, creates data issues, and locks critical insights inside silos. It’s fundamentally at odds with the agility and end-to-end visibility you need to protect yourself in this complex, high-risk environment.
According to Splunk, modern security operations centers (SOCs) must include a common workspace for everyone in the organization. This is crucial, as it removes the need to switch between different tools, eliminates silos, and gives everyone a complete picture of where the security posture stands at any given moment.
As an example, Duck Creek Technologies replaced its existing SIEM solution with Microsoft Azure Sentinel and was able to gain end-to-end visibility across its entire digital estate.
While Duck Creek’s old SIEM also ran on Azure, it wasn’t natively integrated — which meant it was missing some critical functions — like the ability to pull real-time reports or integrate telemetry and log data with other security insights.
As such, combining Microsoft-based data with Azure Sentinel was a game-changer. Defender for Endpoint allowed the Duck Creek team to quickly make adjustments to security policies when COVID forced them to go remote.
And, on top of that, the company can now monitor user activity, log-in patterns, etc. at a glance, from a single pane of glass — providing extra assurance that employees can work remotely, at scale — without taking on any additional risk.
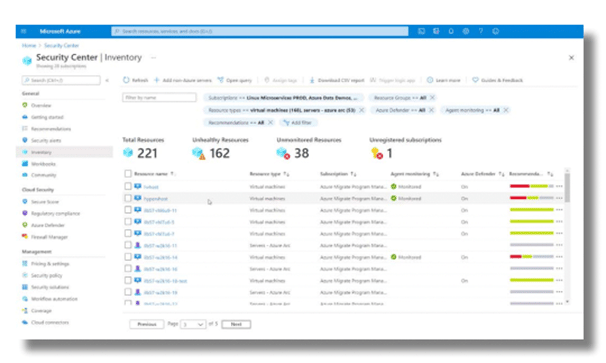
Microsoft’s security solutions can all be managed through the Azure Security Center, which provides centralized monitoring and management across the entire estate.
In the below screenshot, you can see an inventory of all resources across on-premises and cloud environments – all managed using Azure Arc via Azure Security Center.
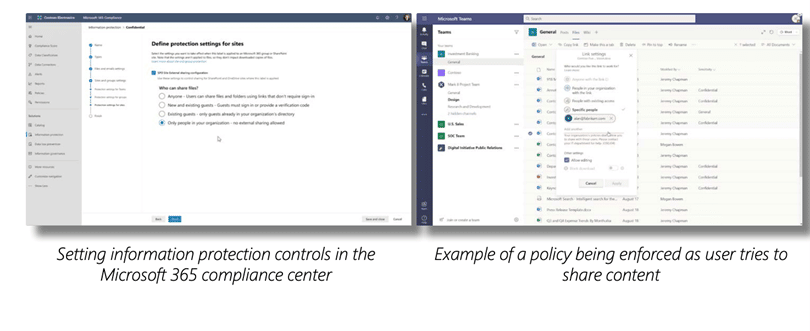
You can also set information protection controls in the Microsoft 365 Compliance Center by creating policies, automating data labeling and classification, and enforcing custom rules using a series of triggers and actions to encrypt files, limit access, or restrict the use of third-party apps.
While tools will vary by organization, you’ll want to make sure that you cover all possible vulnerabilities — from multiple angles. Again, the Zero Trust security pillars are a great starting point for figuring out what to look for when evaluating potential solutions. You can also take this series of self-assessments to determine the maturity of your ransomware strategy – and what it’ll take to improve your defenses against ransomware.
As a certified Microsoft partner, Velosio works directly with clients, helping them evaluate their security posture, identify blind spots and risks, and implement the best-fit solutions. To learn more about working with us, contact an expert today.
Talk to us about how Velosio can help you realize business value faster with end-to-end solutions and cloud services.
"*" indicates required fields