How Does Microsoft 365 Protect Data from Ransomware?
Through a robust suite of baked in security features, Microsoft 365 protects data and digital resources from ransomware in multiple layers.
Table of Content
Microsoft 365 protects data and digital resources from ransomware in multiple layers.
The Microsoft 365 apps themselves come with baked-in defenses that protect customer data from phishing, spoofing, data corruption, and ransomware encryption. OneDrive, Teams, and SharePoint online include built-in virus protection, built-in versioning, and recovery tools.
Microsoft Teams lets admins define data loss prevention policies that prevent users from sharing sensitive info via channels and chats. SharePoint and OneDrive protect docs and data in-transit and at-rest. The list goes on.
But — protecting your system from malware extends beyond the embedded security features that come standard with MS365 apps. Microsoft 365 Threat Protection spans a wide range of security solutions — covering all devices, apps, identities, workloads, endpoints, and data.
In this article, we’ll look at a few solutions you might incorporate into your ransomware defense strategy.
Defender for Microsoft 365 is a unified defense suite built for today’s biggest ransomware threats. It includes everything from threat detection, prevention, investigation, and response across all identities, apps, email accounts, and endpoints – essentially, covering the entire attack chain.
In a 2020 blog post, Microsoft explains that human-operated ransomware campaigns typically start with unsophisticated “commodity” ransomware like trojans that do set off detection alerts and are then quickly triaged by IT without a full investigation.
Additionally, anti-virus solutions might block the initial payloads – but attackers often deploy different payloads until they’re successful. Or – use stolen credentials to enter the system and disable protections.
Defender for Microsoft 365 draws on years of research into high-profile attacks – using key findings to build a solution that addresses all infrastructure weaknesses threat actors might exploit, harden assets, and understand the entire “story” behind each attack.
Inside, you’ll find a ton of impressive features. The incident overview portal combines related alerts from all products, apps, and devices into a single dashboard view.
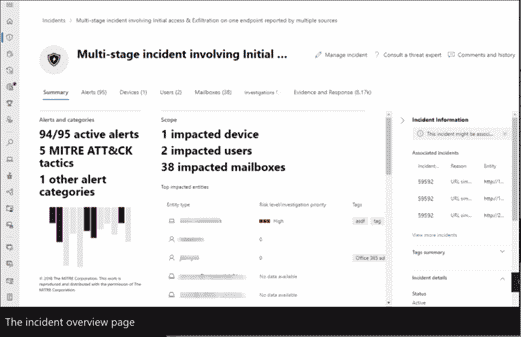
You can also investigate individual alerts within a system-wide incident. For example, here’s an alert for suspected credential theft. For example, here’s an alert for suspected credential theft. It tells you the type of incident (in this case, credential access), the severity, technique, and source – plus a brief description of what that all means.
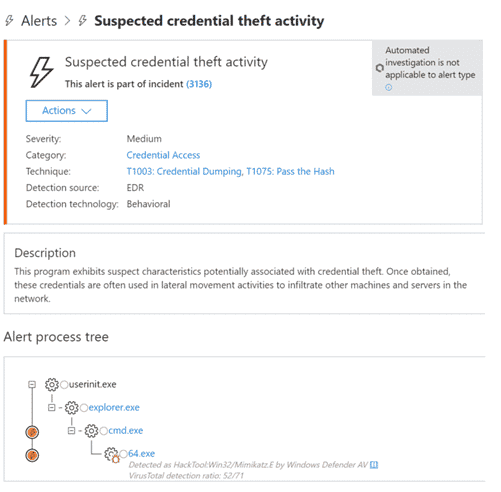
Microsoft 365 Defender also supports AI-driven automations that remediate infected assets back to a baseline security state and cross-product threat-hunting, which allows users to run custom queries to search for signs of compromise.
Microsoft Defender for Office 365 is a cloud-based solution that’s part of the broader Microsoft 365 Defender ecosystem, designed to protect against threats to email and collaboration apps. It uses built-in AI to identify suspicious files and content and analyzes attack patterns and activities to identify ransomware campaigns.
Defender for Office 365 uses a multi-layered protection stack, designed to prevent attacks like credential phishing, email compromise, and advanced malware from infiltrating your system.
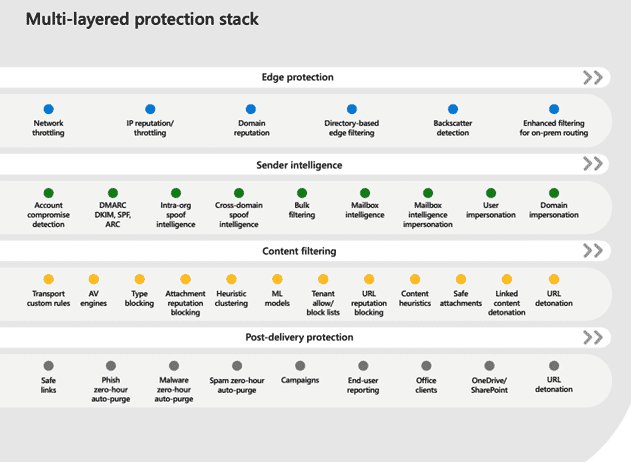
Defender for Endpoint is another Defender 365 service, focused on
Inside, you’ll find advanced cloud security analytics, endpoint behavioral sensors, built-in threat intelligence. Together, these capabilities enable you to ID threat actor tools, tactics, and patterns that can then be used to trigger alerts and inform your defense strategy.
The platform also includes features that make it easy to discover unsecured endpoints and devices connected to your network. You can onboard and secure those devices using integrated workflows. Or – investigate potential threats lurking on newly-discovered devices.
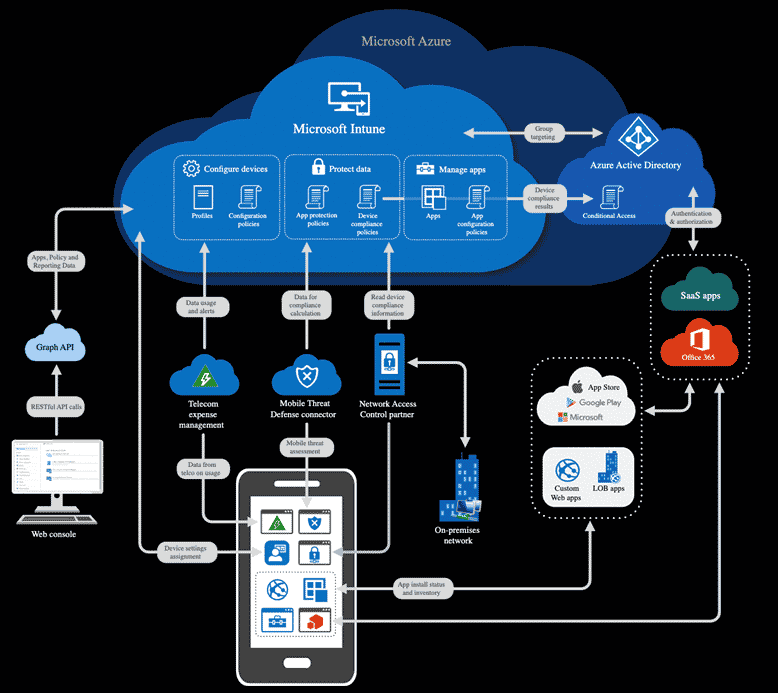
Microsoft Intune is a cloud-based mobile device management (MDM) and mobile app management (MAM). It’s designed to help organizations manage and control how company-issued laptops, phones, and tablets are used and control access to critical apps and data on personal devices.
It can be used across the entire MS365 suite. Meaning, you can deploy apps like Teams, Outlook, or Excel to user devices while at the same time, ensuring that your data is protected by the policies you create.
Intune also integrates with Azure AD, allowing users to control who has access and what they can access.
Azure AD and Intune work together to enable conditional access to email or Microsoft 365 apps.
For example, you’ll define device compliance policies with Intune. The platform evaluates each device against the requirements outlined in the policy and sends status reports to both Intune and Azure AD. Then, within AD, decisions are made re: whether to block or allow access to resources from the device in question.
You can also integrate Intune with Microsoft Defender for Endpoint and review a list of security tasks that identify at-risk devices and prescribe a set of steps for minimizing those risks.
Here’s a look at the architecture to give you a better sense of how Intune works with AD, Defender for Endpoint, and the rest of the Microsoft ecosystem.
Another solution, Microsoft Cloud App Security leverages a built-in catalog of over 17k public apps – along with usage data across all users, devices, applications, and IP addresses in your digital environment. You can use Cloud App Security to discover and identify cloud app usage and identify instances of shadow IT, regulatory noncompliance, unpatched apps, and more.
Here’s a graphic that breaks down how you might use this solution to manage newly discovered shadow apps:
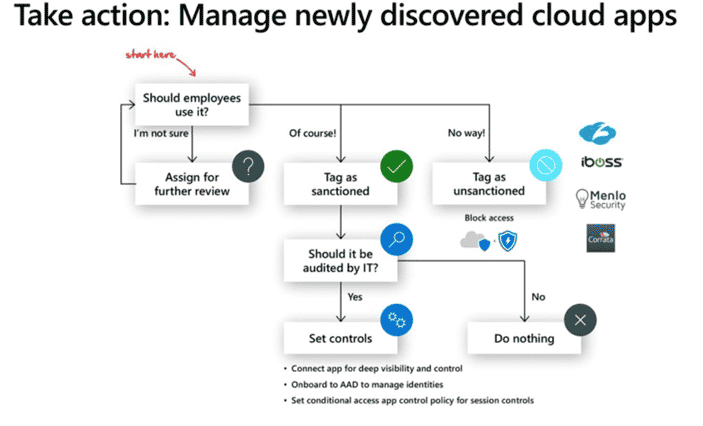
Microsoft 365 apps offer many layers of protection that, together, support secure remote work, detect and prevent viruses, block malware, and respond to threats in real-time.
But – it’s important to note that these capabilities only go so far and apps like OneDrive, Teams, and Outlook can still be infected by malware. It’s on you to educate your team, implement the right policies, and enable identity, endpoint, and device protections.
Velosio understands just how challenging it can be to identify the best tools for securing your system – much less keep track of all the “Defenders.”
Our experts can help you find, implement, and configure the MS365 security solutions you need to protect your stack. To learn more about using Microsoft 365 security solutions to fight off ransomware and other cyber threats, contact us today.
Talk to us about how Velosio can help you realize business value faster with end-to-end solutions and cloud services.
"*" indicates required fields