How Does Ransomware Work?
Explore the workings of ransomware, its consequences for users, and vital measures to defend against this growing cyber threat.
Table of Content
Ransomware is a type of malicious software (malware) that locks users out of their computers or encrypts their files, making them inaccessible until a ransom is paid. Cybercriminals typically demand payment in cryptocurrency, such as Bitcoin, and may threaten to permanently delete or leak sensitive data if the ransom is not paid. Ransomware spreads through methods like phishing emails, malicious links, or compromised websites, targeting individuals and organizations alike.
They’ll then hold those files hostage until the ransom is paid (though, unsurprisingly, there’s no guarantee they’ll keep their word). If victims don’t pay the ransom by the deadline, the attacker will leak the files, sell the data, or take some other damaging action.
Ransomware is a type of malware that spreads through phishing emails, malicious links, or infected websites. Once introduced to your device, it encrypts your data, making it inaccessible. The attackers then demand a ransom, usually in cryptocurrency, in exchange for a decryption key to unlock your files. The malware can also lock your device or steal data, adding further pressure to meet the ransom demands.
From there, the attacker typically makes a threat that reads something like this: if the ransom isn’t received by X date, the files will either be destroyed or sold off.
Now that we’ve provided a general explanation for how a ransomware attack might play out, let’s dig a little deeper.
Below, we break down the “typical” ransomware lifecycle one step at a time – giving you a better idea of how malicious code operates within your system, so you can better protect your org from attacks.
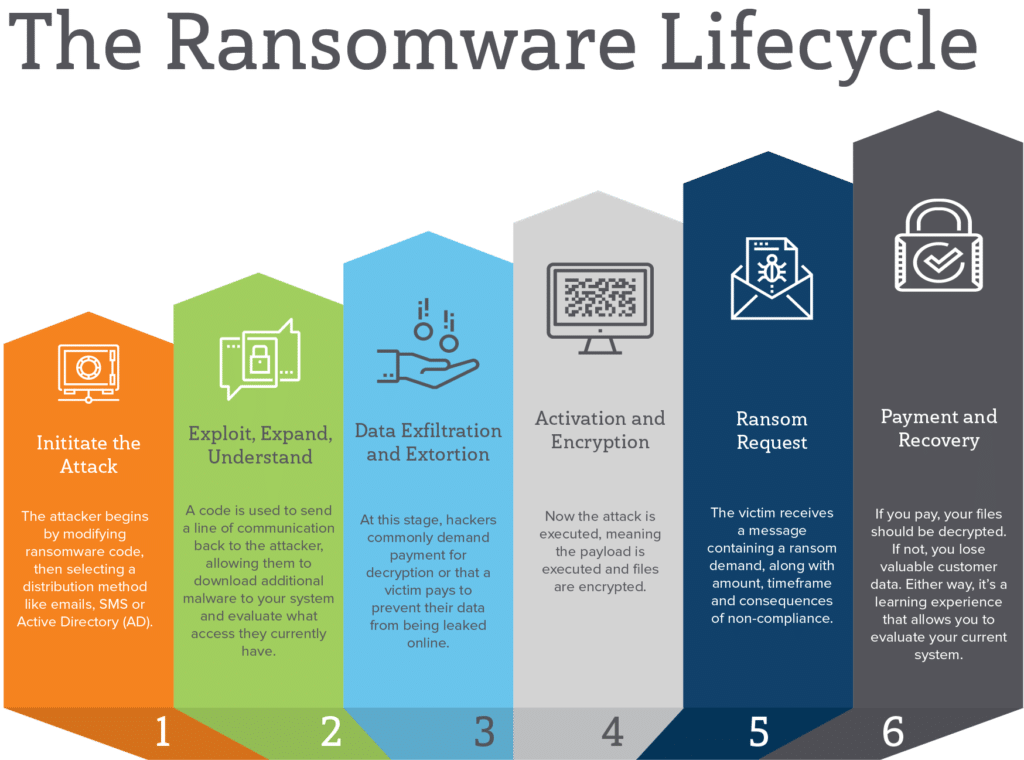
First, the hacker writes or modifies ransomware code based on the system they’re attacking. Then, they’ll establish a distribution method — or how they’ll launch the attack — email, SMS, Active Directory (AD), executable, etc. — and gain initial access.
This can be done in a variety of ways — by setting up malicious websites, exploiting vulnerabilities in your remote desktop connections, or launching a direct attack on weak points in a specific piece of software (i.e. an unsupported app or a system that’s overdue for an update).
That said, the most common points of entry are phishing/smishing campaigns that distribute an access trojan like TrickBot, Bazar, or QakBot.
Attackers tend to target the less technical staff because they’re more likely to click the link or enter contact information. It’s also worth noting that the more users you have in your organization, the more vulnerable it is to a user-targeted attack. All it takes is one mistake from a single user and hackers can execute the code and infect the entire system.
Once the ransomware has gained initial access to your system, the code will establish a line of communication back to the hacker. Think — offensive security tools like Metasploit or Cobalt Strike or a remote access tool (RAT) that allow them to establish remote access to your system.
This stage is about mapping out your local system to determine what they currently have access to, then expanding outward — acquiring additional data and credentials before activating the attack.
The attacker might use this communication line to download additional malware to your system — which could start making lateral moves across your digital ecosystem right away gathering as much data as possible. Or — the malware could lay in waiting for several months — allowing the attacker to strike at the perfect moment.
Ultimately, this is a recon mission where cyber attackers are figuring out how to get the most ransom for their efforts.
Here, ransomware attackers shift their focus from identifying valuable files and data to actually stealing it.
Per IBM’s 2022 X-Force Threat report, almost every ransomware attack X-Force IR has responded to since 2019 has used the double extortion tactic — where attackers steal their victim’s data before the malware activates its encryption routine.
The idea is, hackers can make two demands — first, by encrypting the victim’s files and demanding payment in exchange for decryption. And second, by demanding that the victim pays an additional ransom to prevent the attacker from leaking their data online.
While double extortion attacks are still more common, cyber attackers are increasingly adding on extra layers of extortion — launching triple extortion attacks where attackers demand payment from anyone who might be affected if the victim’s data is leaked. There’s also quadruple extortion — where attackers leak or destroy the victim’s data if they report the incident — whether to law enforcement or the media.
The IBM report also found a fair amount of variation among ransomware attackers where data exfiltration is concerned. Most operators use tools like RIClone and WinSCP, but it seems that custom exfiltration tools are becoming more common — as well as command-line tools like bitsadmin.
At this point, the cyberattacker executes the attack remotely or the victim activates the code, say, by clicking an infected link. Either way, this is the moment in which the payload executes and encrypts the files.
Which means, orgs need to move quickly to mitigate potential damage and recover from the attack. Ideally, you already have a plan in place for containing the damage and getting things back on track – otherwise, you could be looking at hours, days, or weeks of downtime – which, of course, is disastrous for your reputation and your bottom line.
At the same time, a solid action plan won’t necessarily keep you safe. For example, ransomware designed specifically to go after backup systems might also encrypt or delete backup files – preventing a smooth recovery.
In that case, decrypting the data is unlikely – so your only options are moving forward without that data, paying the ransom, or recovering from an older backup or replica.
At this stage, the victim is presented with a message explaining how things are supposed to go down — ransom demands, amount, timeframe, a wallet/transfer method for sending the money, and, of course, the consequences of non-compliance.
Depending on the form of currency and how the funds are dispersed it’s often sent into the digital void. It’s important to note that cryptocurrency is largely untraceable due to the decentralized nature of the blockchain.
At this point, things can go a couple different ways. If you opt to pay the ransom, your files are decrypted (well, at least they’re supposed to be), you’ll report the breach to law enforcement, update your CyberSec reports, and, hopefully, learn from this experience.
Recovering funds is rare, but it is possible. Law enforcement has had some success here – most notably with the Colonial Pipeline attack). In that instance, law enforcement was able to recover 63.7 of the 75 BTC (or $2.3M) as the price of Bitcoin dropped shortly after the attack. So, yeah, even if everything goes according to plan, you could face major losses based on crypto’s inherent volatility alone.
If you don’t pay the ransom, you lose the stolen data, and valuable IP and/or customer data is released into the wild, sold, or both. Your company’s reputation takes a big hit. You’ll likely lose customers and the public’s trust (aka it’ll be so much harder to replace customers after they jump ship). And then, there’s the matter of regulatory fines, lawsuits, and losses.
Now, keep in mind that paying the ransom or even recovering data from a backup doesn’t mean you’re in the clear.
Resale is still a possibility even with payment. There’s not always definitive proof that the attacker doesn’t have an unencrypted copy of the data. And – the more valuable the information, the higher the risk of resale.
There could still be ransomware code or malicious files hanging around in your system and you’ll want to make sure you remove them – and seal up any remaining security gaps or vulnerabilities before moving forward.
That said, the attack itself can give you an idea of what type of ransomware hit your system, making it easier to track down and remove. But – it’s a good idea to do this inside an isolated sandbox environment to clean up your system to protect against the risk of reactivation.
Ransomware attacks can infiltrate your system – even with the best protections in place. Understanding how ransomware works – from infiltration to activation, encryption, and beyond – is an important step toward preventing attacks from happening in the first place.
It can help you map out critical endpoints, vulnerabilities, users, and credentials so you can better secure them. More importantly, it allows you to ensure that security is embedded in the flow of daily work – both by making security a central part of your culture and by embracing solutions that make it easy for everyone to practice good habits.
Velosio’s Microsoft experts help clients identify and implement secure solutions that not only keep your business safe in the cloud – but actively generate value for your customers and outperform the competition.
Talk to us about how Velosio can help you realize business value faster with end-to-end solutions and cloud services.
"*" indicates required fields