How Entra Safeguards Your Business From Ransomware
Discover how the three solutions In Microsoft Entra protect multi-cloud environments against ransomware attacks.
Table of Content
Microsoft Entra consists of three core products: the familiar Azure AD – along with two new solutions, Microsoft Entra Permissions Management and Entra Verified ID.
It’s a rebrand of Microsoft Identity Solutions – designed to tackle identity and access management (IAM) on multiple fronts – without adding friction to workflows and daily interactions.
Crucially, Entra was built with modern cyber threats in mind – ransomware gangs, nation-state attacks, cloud-specific vulnerabilities, and so on.
Microsoft’s 2021 Cyber Signals report declared identity the “new battleground.” Researchers say there’s this “dangerous” gap between identity-focused ransomware attacks and preparedness of would-be victims.
Proofpoint researchers seem to agree, noting that Microsoft 365 and Google Workspace accounts and single sign-on (SSO) apps are heavily targeted by ransomware attackers because they house valuable data, user credentials, and business communication logs.
Threat actors still rely on simple tactics like phishing and social engineering to steal easily-guessed (or default) passwords.
What’s especially troubling is that, even if just one person sets their password to something like “password,” hackers can penetrate the network and access even more valuable credentials, steal and encrypt even more data, and, in turn, demand higher ransoms from multiple targets.
Here, we’ll look at how all three solutions protect multi-cloud environments against ransomware attacks using Entra.
Microsoft Azure Active Directory (aka Azure AD) is a comprehensive, cloud-based IAM solution designed to support application access permissions, directory management, and advanced ID protection. Azure AD provides a unified platform for managing and securing identities across all user groups, apps, and devices — both on-premises and in the cloud.
Real-time insights into content usage, incoming threats, and unusual behavior allows users across the entire organization to avoid blind spots that put them at risk – and take the appropriate action.
IT teams benefit from greater visibility, tighter controls, and built-in automations that simplify and reinforce identity governance, provide secure, hands-off user provisioning, and apply adaptive access policies based on real-time risks.
On the end-user side, Azure AD actively supports team productivity. SSO, for example, allows employees, partners, clients, customers, etc. to access everything they need with one login. There’s also the option to go passwordless – using biometrics to access critical apps and info. Either way, users aren’t spending their time juggling a bunch of usernames and passwords. Nor are they signing into multiple apps every day.
Microsoft Entra Permissions Management is a cloud infrastructure entitlement management (CIEM) solution for monitoring, managing, and protecting identities and permissions across all apps and services in one centralized hub.
Permissions Management offers granular visibility into all actions performed by every identity, app, or resource and tight IAM controls across all cloud environments (Azure services, of course, but also Google Cloud, AWS, and others) connected to your network.
The platform also makes it easy to assess permissions risk by evaluating permissions against actual usage, track anomalies and generate detailed forensic reports, and establish and enforce right-size permissions based on real user needs.
Microsoft Entra Verified ID (currently in public preview) is a decentralized identity solution that helps orgs quickly issue and authenticate users credentials, to protect against ransomware. Think — personally identifiable information (PII), certifications, degree requirements, work history, and other key details. And at the same time, ensures that individual users are in control of their own identities – and protected on an individual basis.
Decentralized identity represents a shift away from companies owning all credentials to users controlling their digital identities themselves.
Instead, a decentralized network of businesses, institutions, organizations, governments, and individuals serve as issuers and verifiers for verifiable identity credentials, while the end-users themselves grant permissions and manage access through their own digital wallet.
How it works is:
This diagram breaks down the basic relationship between these three players (check out Microsoft’s Decentralized Identity white paper for full details re: what, why, and how Verified ID works):
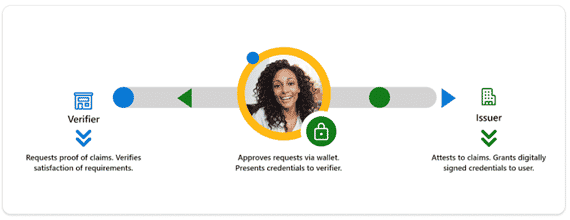
Per a recent Bank Info Security article, the rise of decentralized ransomware attacks demand decentralized protections. When orgs rely on centralized IAM solutions and perimeter defenses (i.e. network-level firewalls), any type of ransomware — be it well-known strains or new variants — can cause significant damage.
If attackers steal credentials from a single user and deploy malware capable of spreading, it can rip through your entire system, your customers’ systems, and, potentially, the systems of any other orgs that use the same apps or cloud provider.
When protections are applied at the individual level, hackers and verified by a trusted, independent party, malware can’t move laterally through your system and it’s much harder for attackers to tunnel into a different network with shared vulnerabilities.
Microsoft Entra helps users beef up ransomware protections per Zero Trust best practices – without introducing unnecessary complexity or friction to administrators or users. But – you’ll need to map out your threat landscape and lock down every endpoint to capture the full range of benefits the Entra suite has to offer.
Velosio’s cloud consultants can help you understand where your IAM efforts are falling short — and what you can do about it. Our experts will review all apps, services, and infrastructure. Then from there, they’ll work closely with your team to develop a cybersecurity roadmap, implement the right solutions, and even provide training and ongoing support.
Talk to us about how Velosio can help you realize business value faster with end-to-end solutions and cloud services.
"*" indicates required fields