Practical Approaches for Detecting Ransomware
Discover steps you can take when detecting ransomware – and take action against incoming threats before real damage is done.
Like any virus, early detection and swift action is your best bet for making a full recovery after a ransomware attack. The thing about detecting ransomware is, it tends to hide out in your system until the threat actor decides to launch the payload. Ransomware might lie dormant for a few days or several months.
But often the aim is to catch victims off-guard so hackers can move quickly through the system before anyone catches on.
That way, they can steal more data, encrypt more files, and demand higher ransoms from desperate victims willing to pay almost anything to get their business back on track.
In these next few sections, we’ll look at some of the steps you can take to level up your ransomware detection game – and get ready to take action against incoming threats before any real damage is done.
Cybercriminals are constantly evolving their strategy based on lessons learned from prior attacks, new tools and tactics, and fellow “practitioners.” This means, you’ll need to approach detection from all sides in order to take action against threats.
According to Crowdstrike, there are three main ways to detect ransomware — and you’ll need to incorporate them all into your strategy so nothing falls through the cracks. Here’s a quick look at each type and where it fits into the broader detection and response strategy:
1. Signature. Malware comes with a unique signature that includes IP addresses and domain names, as well as other identifying factors. Signature detection tools analyze the active files running on a machine against a library of pre-existing signatures to identify the presence of known malware. This approach focuses exclusively on known threats, leaving systems wide open to new variants and novel strains.
2. Behavior. Ransomware behaves in unusual ways — moving laterally across the network, opening and encrypting files. Behavioral detection tools monitor systems, flag unusual activity, and sound the alarms when human intervention is needed.
3. Abnormal traffic. Abnormal traffic detection is similar to behavior, but focuses on detecting unusual activity at the network level. These days, many ransomware attacks follow a two-pronged approach — first, stealing valuable data for resale or leverage, then encrypting the data and demanding that victims pay a ransom.
This double extortion model results in large data transfers to external systems. But — even if the ransomware is set up to conceal those transfers, it may still generate network traffic that can be tracked.
Tools with abnormal traffic detection capabilities allow you to follow a trail back to the ransomware hiding inside a specific machine — then delete it and start working toward recovery.
Organizations need both a high-level view across all networks, devices, identities, environments, endpoints, etc. – anything connected to their business, however tangentially – to prevent, detect, and respond to security threats – and granular visibility into each of these components.
According to Microsoft’s Azure Defenses resource, ransomware triggers some obvious changes in your system – lockouts, alerts, or notable changes in basic system behavior. Common signs of an attack include:
While many of these signs seem like obvious evidence of ransomware, they can easily slip through the cracks if you’re not working from a unified security stack.
Cyber criminals target different risk vectors. Cloud environments and storage solutions are the most common ransomware targets, as are misconfigurations and unpatched software. Attackers scan for vulnerabilities they can use as access points – they don’t necessarily care whether that entry point is a weak spot in your infrastructure, an unsupported legacy app, or a cyber-unaware employee.
Different signs also show up in different places – security logs, identity and access management platforms, individual SaaS apps, etc. When you’ve got security silos or poorly-integrated solutions, you don’t have the visibility you need to look for high-level patterns that indicate there’s been an attack. You can’t identify and fix vulnerabilities before they become a problem or proactively make improvements that can strengthen your overall security posture.
Now, different orgs might use different types of analytics solutions to identify and act on cyber threats. Those solutions should be chosen based on factors like business model, regulations, and the unique risks of operating within a specific industry. For example, financial services firms might use AI insights to mitigate fraud risks or detect unusual transactions and behaviors.
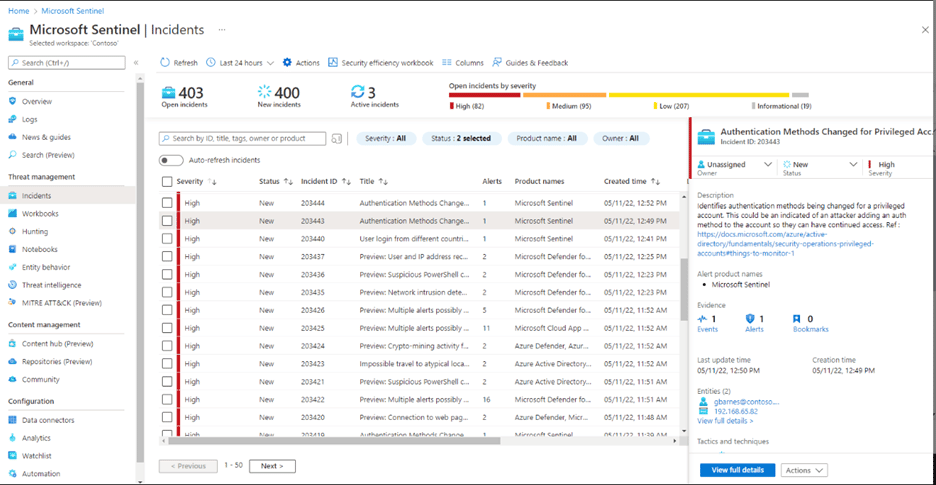
But, when it comes to detection and response, Microsoft’s SIEM and XDR solutions – Azure Sentinel and Microsoft Defender – play a critical role in helping you identify and contain ransomware.
Microsoft Sentinel comes with 200+ built-in connectors that enable estate-wide monitoring across all apps, devices, users, and environments – both on-prem and in the cloud. Users can easily detect threats using the platform’s built-in analytics and gain contextual and behavioral insights into threat actors and threats.
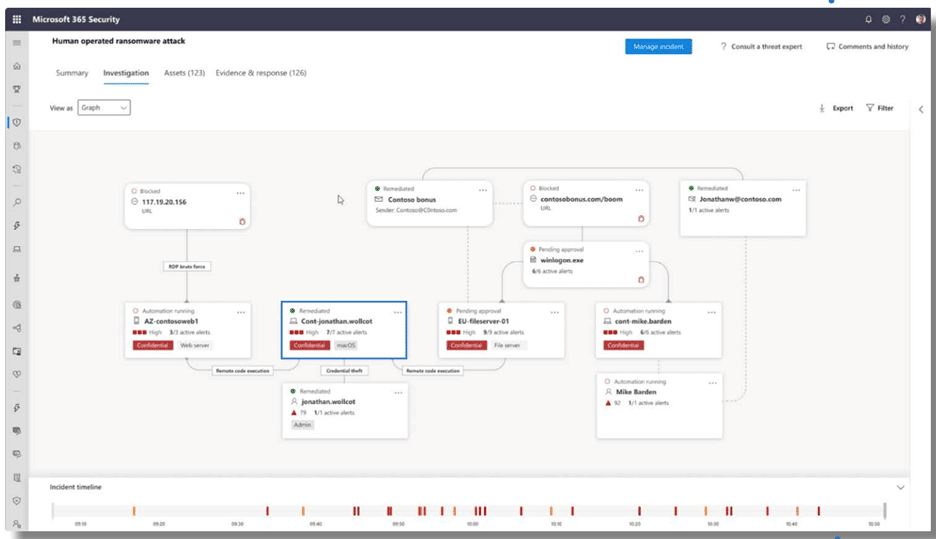
The screenshot below depicts an investigation into a human-operated ransomware attack via Microsoft Defender. The XDR solution can identify and contain breaches discovered on a specific endpoint, and from there, take steps to return the infected device back to a trustworthy state before connecting back to the network.
Detection isn’t just about tools. Just look at the SolarWinds attack. At the time of the breach, everything was working as it was supposed to. Yet, the Orion update still became the point of infection. The incident wasn’t so much a failure of technology, as it was a failure of people and processes.
While effective detection capabilities are crucial when it comes to detecting attacks, cyber-hygiene is just as important – if not more.
Employees should always be on the lookout for anomalies like unfamiliar data or odd-looking files to aid in ransomware detection. And, of course, they should be trained in best practices such as never entering credentials into unsecured websites or how to identify potential phishing campaigns.
Beyond the basics, organizations should put together a comprehensive response plan – with playbooks for dealing with different scenarios.
For example, monitoring is a total game-changer for customers. But – only if employees are prepared to properly work with real-time insights and take action against threats. It’s important to understand that there’s much more to this process than implementing an SIEM or setting up a security operations center (SOC).
Organizations must ensure that the proper configurations and procedures are in place – and that employees understand how to use monitoring tools, AI, and machine learning – and are empowered to move quickly in response to an attack.
They should also test users’ understanding of risk. For example, running simulations that test their response to phishing campaigns or how to contain threats, based on which attack vector was used as the initial entry point.
According to a Forrester report commissioned by Secureworks, organizations face many security challenges including detecting and responding to unknown threats and attacks.
60% of respondents reported their lack of understanding in this area is currently limiting their ability to adequately secure their digital estate, while 59% said their lack of expertise is preventing them from reaching security goals. 23% of IT leaders admitted security operations rely on several manual processes – which leads to scalability issues, among other problems.
This data highlights the urgent need for organizations to streamline and automate security operations – particularly as orgs, already short on time, struggle to master the skills needed to stay safe in today’s complex security environment.
Automation plays a key role in protecting your company against cyberthreats. It’s used to prevent, detect, contain, and act on incoming threats. It’s also become a vitally important tool for coping with the growing number and sophistication of cybersecurity threats.
According to Zero Trust principles, automation simplifies and strengthens an organization’s security posture. Cloud-based intelligence and AI can detect and respond to anomalies in real-time, while automated alerting and remediation capabilities can reduce the mean time to response (MTTR) to incoming attacks.
With Microsoft Sentinel, users can correlate alerts into incidents and automate and orchestrate common tasks using custom playbooks. Playbooks are designed to help SOC analysts and engineers automate and simplify tasks like data ingestion and enrichment, investigations, and remediation. They allow users to set up custom automation rules to triage incidents, assign action items to the right person, and label incidents as known false positives, severe threats, etc.
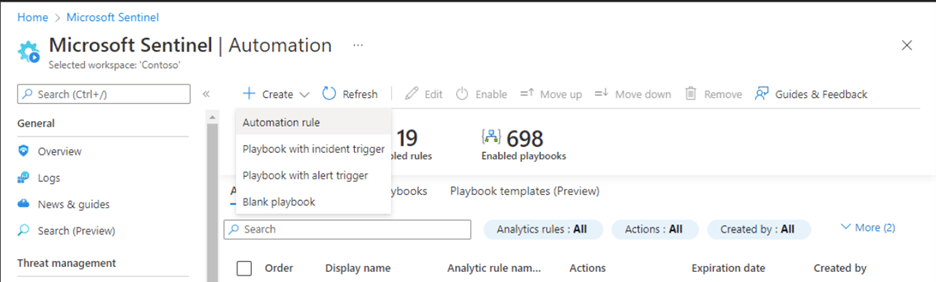
Building on the themes of AI and automation, you’ll want to set up alerts on high-risk anomalies or behaviors so that nothing suspicious falls through the cracks.
Some solutions provide contextual alerts and insights into attacker behaviors.
For example, Microsoft Defender can raise alerts and prioritize actions, keeping businesses safe in the cloud – while also saving admins a ton of time.
For example, the platform can automatically detect unusual activity and send alerts to relevant users. Those users can then take action to stop the virus from spreading to critical docs, data, IP, etc. – containing the threat, removing the malware, and restoring the impacted data from a safe backup.
But – one 2021 Microsoft Security blog brings up an important consideration: you’ll want to make sure you take steps to reduce “alert fatigue” within your organization. Otherwise, your people will stop paying attention after one too many false positives. According to the blog post, Microsoft already employs several strategies via its integrated SIEM and XDR solutions to minimize alert fatigue among customers.
For example, native integration between ransomware solutions allows customers to connect the dots between disparate data sources and threat signals, grouping alerts from across the threat landscape to tell a complete story about what happened and why.
Azure Sentinel’s built-in machine learning automatically detects and analyzes threats – identifying combinations of suspicious behaviors and actions at different stages in the kill chain. It then uses those findings to reduce signal noise and improve alert quality over time.
Ransomware detection best practices and tools help companies detect malware early in the game, allowing them to contain the threat and take steps to re-establish business continuity before any serious damage is done.
But – it’s important to understand that early detection won’t do you much good if you’re not prepared to take action. Ransomware moves fast. Every second you lose is potentially a major blow to business continuity and the bottom line.
We’re talking: data loss, irreparable damage to critical documents or IP, credential theft, data leaks that involve customers or partners – and all of the fallout that comes with the territory.
Microsoft offers several security solutions you can use for detecting ransomware and response strategy.
As a Gold-Certified Microsoft Partner, Velosio can help you evaluate those solutions and implement the most effective security stack for your business.
{
“@context”: “https://schema.org”,
“@type”: “VideoObject”,
“name”: “Leveraging Microsoft’s Toolset to Protect Your Business from Cyberattacks”,
“description”: “Learn how technology can be used to increase protection and security from cyberattacks. Here, we highlight the cybersecurity toolsets within the Microsoft Ec…”,
“thumbnailUrl”: “https://i.ytimg.com/vi/V-FpAxfphDQ/mqdefault.jpg”,
“duration”: “PT44M47S”,
“contentUrl”: “https://www.youtube.com/watch?v=V-FpAxfphDQ”,
“embedUrl”: “https://www.youtube.com/embed/V-FpAxfphDQ”,
“uploadDate”: “2023-01-11T07:44:38-08:00”,
“potentialAction”: {
“@type”: “SeekToAction”,
“target”: “https://youtu.be/V-FpAxfphDQ?t={seek_to_second_number}”,
“startOffset-input”: “required name=seek_to_second_number”
}
}
Talk to us about how Velosio can help you realize business value faster with end-to-end solutions and cloud services.