Ransomware Protection in Microsoft Dynamics 365
Dynamics 365 enables you to manage and secure your business on a holistic level. That’s a big deal when defending against ransomware.
Table of Content
Modern cloud ERPs house everything from core financials, valuable IP, and sensitive data, to the collaboration apps, customer records, and email accounts employees use every day.
Having that unified system in place is a prerequisite for any kind of digital transformation. You’ll need an org-wide data ecosystem and deep integration across your entire network to benefit from now-essential tech like AI, ML, real-time data streams, and intelligent automations.
At the same time, it’s a major liability.
ERPs contain mountains of valuable data and power the full spectrum of daily operations, so naturally, they’re a frequent target for ransomware attacks.
Microsoft Dynamics 365 consolidates your entire business into a single cloud-based platform – allowing you to manage, control, and secure all apps, devices, accounts, and data on a holistic level. That’s a big deal when it comes to defending against ransomware.
Read on and we’ll explain why.
We know that threat actors exploit security gaps created by outdated, on-prem tech, and siloed systems, platforms, and processes.
We also know that shadow IT, unsecured endpoints, unsupported apps, and so many other vulnerabilities make it easy for attackers to slide right into your system and do some serious damage.
Cyber criminals often use distributed denial-of-service (DDoS) attacks to target ERPs linked to critical infrastructure or services (Colonial Pipeline is a prime example). Attackers go after public-facing endpoints, rendering resources like power grids or industrial production lines unusable.
ERPs can also be susceptible to phishing, credential theft, or cloud ransomware attacks as they typically connect to file storage, email, and other productivity apps.
Dynamics 365 provides end-to-end visibility across the entire business — an important first step toward building a strong Zero Trust policy.
This allows IT to map out the entire estate — devices, identities, data, infrastructure, etc. — they didn’t miss any shadow apps or stray endpoints. Admins can then start monitoring user behavior, identifying vulnerabilities, and analyzing the metadata to learn more about the movement and origins of previous attacks.
From there, they can start adding in multi-layered protections like data encryption, multi-factor authentication, firewalls, SIEM and XDR, etc. to prevent hackers from moving laterally through the system — or worse, hiding in some dark corner for months, waiting to strike.
And later, IT can start actively hunting for threats, investigating incidents, and using real-time analytics to find and fix vulnerabilities that put the business at risk.
Out-of-the-box, Dynamics 365 apps come with the same basic application and data security protections including:
D365 Finance & Operations includes everything we just mentioned – but because it’s built to support large enterprises, subscribers gain access to Microsoft Lifecycle Services (LCS) for configuring, monitoring, and managing your security environment.
Inside, you’ll find several advanced features, embedded AI, built-in automations, testing and diagnostics tools, a business process modeler, and more.
The idea is, that the bigger the organization, the harder it is to identify, much less secure, all of the moving pieces connected to your network. Dynamics 365 Business Central caters to SMBs, which, in most cases, don’t need all of these extra features to detect and prevent ransomware attacks.
But – D365 BC offers limited reporting capabilities and few out-of-the-box automations. You’ll definitely want to set up the Power BI integration ASAP to ensure that you’re able to get that granular visibility into your entire business.
It’s not a bad idea to sign up for Power Automate, as well as Azure solutions like Microsoft Sentinel, Defender for Cloud, or Azure DDoS Protection, either.
Read our post on D365’s security capabilities for a closer look at specific features.
So, the D365 suite includes both ERP and CRM modules (aka Dynamics 365 Customer Engagement, or CE. For enterprise users, modules are purchased a la carte — allowing them to build a flexible system that aligns with their specific needs.
While D365 modules can be purchased and used on their own, they’re part of a broader ecosystem. It’s designed so that users start with the ERP “base,” then add on CE apps to support specific business units like sales, HR, or marketing. D365 CE doesn’t include LCS – and as a standalone solution, it’s siloed-off from critical financial data and operational processes – so benefits are limited to things like access permissions and data encryption.
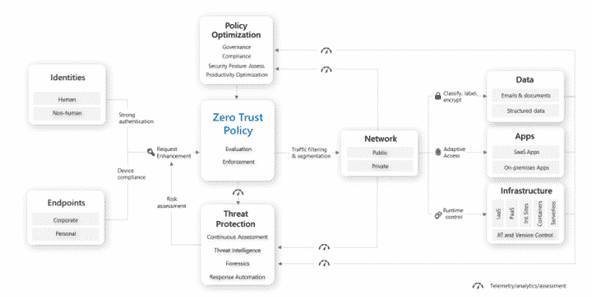
D365 also integrates seamlessly with Microsoft 365 and can be extended with Azure and the Power Platform. We’ve talked about this idea of combining Microsoft apps with each other and the core ERP to unlock new capabilities in the past — but that layered construction is crucially important when it comes to cybersecurity.
While every stack is different, you’ll need to make sure that threat protection, threat intelligence, automation, and policy enforcement are embedded across your entire network.
To give you a sense of what that might look like, here’s Microsoft’s Zero Trust architecture:
Whether you opt for D365 BC or F&O, Microsoft Dynamics 365 provides a strong foundation for building a secure digital workspace in the cloud.
It’s also worth noting that half-baked security strategies, small configuration errors, excessive permissions, and other cyber missteps can override Microsoft’s built-in ransomware protections.
For best results, you’ll want to work with a Microsoft partner that specializes in your industry and has deep expertise in both cybersecurity and Dynamics 365.
Velosio experts work closely with your team to amplify the impact of your Dynamics 365 investment and help you extract more value from your data. Get in touch to learn more about our solutions, services, and what it’s like to work with us.
Talk to us about how Velosio can help you realize business value faster with end-to-end solutions and cloud services.
"*" indicates required fields