Top Security Challenges for Professional Services Companies
In this article, we’ll look at some of the top security challenges professional services orgs are up against right now.
Table of Content
Professional services firms are vulnerable targets for cyber criminals for a few key reasons.
For starters, this is an industry that deals in valuable information. Knowledge workers typically rely on some combination of client data, original research, and proprietary IP to deliver insights and solutions that drive specific outcomes. In other words, firms are sitting on a data gold mine — and threat actors know it.
Beyond the obvious appeal of valuable (and potentially sensitive) data, cyber criminals often see professional services orgs as easy targets. Many work on client websites, conduct business on mobile devices with few protections, and rely on a distributed network of remote workers.
Additionally, security may not be a top priority — particularly in smaller firms with fewer resources. Often, we see orgs focus on productivity — serving clients, delivering projects on-time, attracting new business, etc. — rather than, say, continuity planning or investing in more robust security protections.
In this article, we’ll look at some of the top security challenges professional services orgs are up against right now.
Poor visibility is bad news for professional services firms on multiple fronts. It’s a common root cause for all kinds of problems from revenue leakage and inaccurate forecasting to unpredictable pipelines and project delays.
So, it shouldn’t come as a surprise that visibility issues are one of the top security threats for professional services firms.
In a 2021 survey, Tripwire researchers evaluated cloud security practices across 300+ enterprises. According to their findings, 73% of orgs operate in a multi-cloud environment yet only 9% consider their internal teams “experts.”
What’s interesting is, participants overwhelmingly cited risk as their primary reason for embracing multi-cloud solutions — though 98% say relying on multiple cloud providers created more security challenges.
That kind of “best-in-breed” approach blocks visibility, and, by extension, creates numerous security challenges for professional services companies.
We’ve talked about this before, but firms using a patchwork of unrelated cloud apps face major challenges when it comes to operationalizing their data. And as a result, they lack the real-time insight they need to make critical decisions on the spot.
Shadow IT (particularly among C-level executives) is another source of visibility problems.
AI and automation can help firms rein in shadow IT – but as you can see in the graphic below, getting to a place where you can effectively leverage AI automations against shadow IT (or any other challenge) is a multi-stage journey.
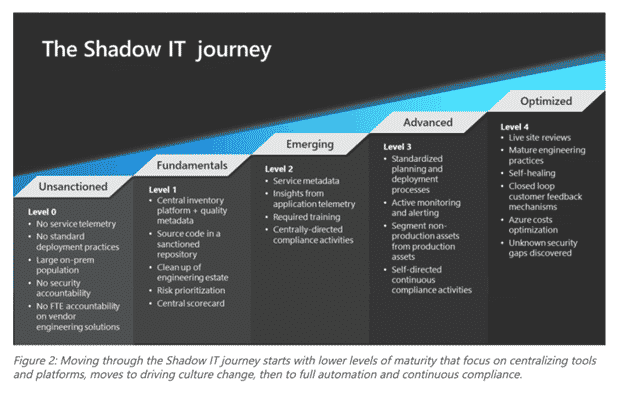
Per a recent report by Deep instinct, firms must embrace a prevention mentality to navigate increasingly complex security challenges — otherwise, incidents like ransomware attacks or insider fraud can cause far more damage.
Savvy orgs are shifting away from reactive threat detection and response strategies and toward something much more proactive. Historically, security teams have been hesitant to make proactive changes — often out of fear they might break something.
Today, IT teams can use real-time data to take proactive actions against ransomware attacks, breaches, and insider threats — and, in many cases, create value for the business and its customers.
That said, firms can’t reap those benefits until they’ve achieved end-to-end visibility, verified the integrity of their data, and have a “single pane of glass” for managing all security — across every app, service, and cloud environment in their digital ecosystem.
Historically, compliance challenges (along with the sensitive nature of the work) has kept professional services firms out of the cloud, tethered to the office, and unfortunately, vulnerable to cyber threats.
And for many firms, it was COVID that pushed them to make the move in the first place. And – as a result, a lot of those companies have yet to master basic cybersecurity hygiene.
This “cloud learning curve” creates other problems, including skills shortages, poor visibility, and a continued reliance on legacy solutions and outdated strategies – all of which makes them more vulnerable targets.
According to Microsoft, two-thirds of cybersecurity pros say hybrid work has made their business less secure. Over 60% of respondents said that the cloud is the most vulnerable part of their digital ecosystem, and 45% say email and collaboration tools, specifically, are most likely to be the target of an attack.
Experts acknowledge that, yes, email and collaboration tools are more frequently hit by malware attacks, but are less likely to cause significant damage than attacks on IoT infrastructure, supply chains, or cloud providers.
While the cloud is safer than ever, it is vulnerable to a new set of threats – so you’ll need to make sure you’re investing in solutions built to defend your firm amid the current conditions.
When workers go remote, devices, apps, and services are no longer contained in the “perimeter,” the threat surface expands exponentially and legacy solutions like network-level firewalls no longer provide adequate protection.
Microsoft says firms must accept that vulnerability is a fact of hybrid work and instead, focus on improving their security posture. So – that might mean embracing Zero Trust principles, embedding security into all aspects of the business, and implementing solutions like SharePoint, Teams, and Azure AD that boost productivity and keep everyone safe in the cloud.
Business consultancy, Capita’s “new ways of working” initiative involved a total transformation of its IT infrastructure and support for its newly remote workforce. The firm built their new hybrid environment around solutions like Azure Active Directory and Microsoft Intune – allowing them to not only improve security, but boost productivity and unlock cost-savings.
Capita Communications Manager Lucie Peters adds that, from a consulting perspective, experts can now demonstrate proven IAM solutions to clients. Because the firm specializes in IT and digital transformation, they can monetize new knowledge and skills – helping clients leverage Azure AD and other Microsoft Security solutions to power their own transformations.
According to Deloitte, the risk of ransomware and data theft – for both client data and valuable IP – are serious threats to pro services organizations. Threat actors target front-office operations like proprietary algorithms, portfolio management, client reports and communications, as well as back-office operations like accounting, finance, HR, business planning, and marketing. Additionally, things like payments, invoices, compliance reports, audit logs, risk models, PII, corporate IP, etc. are prime targets for attackers.
Propublica research revealed that identity theft, in general, has been “surging” since the earliest days of the COVID crisis, but that massive quantities of stolen data were undefended. We can’t say why, exactly, orgs fail to protect their data but it’s likely a combination of shadow IT, data silos, and weak data management policies.
Microsoft experts say protecting sensitive data starts with end-to-end visibility.
Firms need to figure out where critical data lives, classify sensitive info, and from there, implement proper protections. Again – comprehensive analytics, IAM solutions like Azure AD, and eventually, automated governance, threat detection, and issue resolution.
In a recent white paper, Microsoft points out that digital relationships depend on trust. All organizations – regardless of industry – have an obligation to protect client data. But, professional services firms work with clients on a much deeper level than most businesses. It’s not just about protecting PII and tracking data – firms need to create a safe environment for collaboration and implement protections like expiring permissions, data encryption, and secure portals for sharing valuable information.
Beyond that, it’s important to remember that customer expectations about how orgs should handle their data and external collaboration are evolving. Firms need to focus on eliminating friction in the collaboration process and look at cybersecurity as an important part of the client experience.
Arguably, people represent the biggest security challenge facing professional services companies.
According to Infosecurity Magazine, the most common cause of a data breach is human error — whether that’s due to a lack of education and training or poor oversight.
As an example, email is still a big risk because many employees either received cybersecurity training a long time ago — or never received it in the first place. Even though phishing attacks have been around forever, cybercriminals still get results from this tried and true method. What has changed is that malicious emails and attachments look way more legit than they used to.
This Kaspersky blog points toward one common security blind spot: interns. Interns might work with companies for a few months and are replaced by a new cohort when it’s time to move on.
What happens is, admins issue credentials as part of the onboarding process and fail to deactivate those accounts when people leave. That means interns can still access docs and data after the relationship ends and it creates additional opportunities for cybercriminals to steal credentials and infiltrate your system.
Do note that anyone you work with on a temporary or one-off basis — outsourced teams, agencies, contractors, freelancers — present those same risks.
Insider fraud is another big security threat. In some cases, hackers do approach employees to assist in a ransomware attack by posing as someone else (that person’s boss, a client, a financial institution) — much like your average phishing email. Though, typically, it’s malicious insiders, not external cybercrime rings, behind the crime.
Tackling insider fraud requires firms to implement technologies like continuous monitoring tools and AI-driven threat detection — and create a culture where employees are respected, valued, properly compensated, and where responsible data use is the norm.
Zero Trust “trusts” nothing by default — operating on the principle that you should always assume there’s a breach — and act accordingly. A key part of this strategy is identity and access management. Security teams must actively govern access levels and credentials, monitor user activity, and continuously verify user IDs.
Again, firms are paid to share knowledge, insights, and valuable data with clients. Even if much of the work gets done during 1:1, in-person engagements, experts still send reports, presentations, and sensitive info to clients.
There’s no guarantee that those clients follow cybersecurity best practices themselves — working with at-risk businesses undermines Zero Trust strategies, even if you’ve mastered its core principles internally.
Gartner advises firms to develop a list of signature behaviors tied to desired outcomes – essentially, providing clear examples of how employees can take action against cyberthreats.
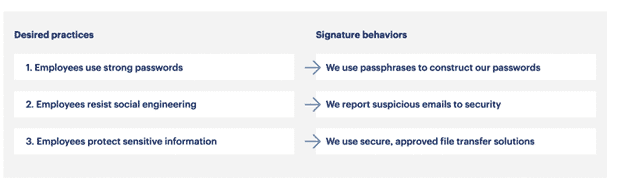
Additionally, linking cybersecurity awareness with tangible business benefits can help you get buy-in from non-technical teams. Here’s a sample featured in that same Gartner report:
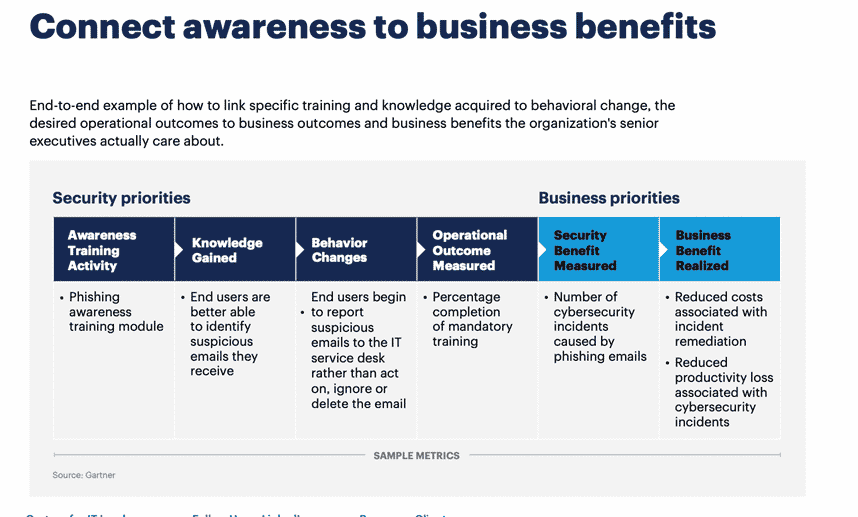
Finally, it’s important to mention the critical importance of selecting vendors that prioritize cybersecurity best practices, and implement effective IAM controls, monitoring, etc.
Generally, you’re in the clear if you find a certified partner via AppSource, but you’ll still need to do your due diligence before you commit. You also should be aware of the fact that working with a partner demands significant effort on your part.
In this case, a good partner is an expert in cybersecurity and Microsoft solutions. They’re not experts in the inner workings of your organization, your clients, or your strategic goals.
Professional services firms can tackle their biggest security challenges much in the same way as other challenges like resource management, forecasting, or project accounting.
Like every digital strategy, cybersecurity is highly data-driven. Meaning, everything ties back to the basics: a strong data foundation, end-to-end visibility, and a unified ERP system. Then from there, you can layer different protections based on your firm’s unique needs, regulatory requirements, and goals.
Velosio experts will help you select and implement the right security solutions for your firm — and ensure that all endpoints, devices, identities, and data are visible, secure, and easy to manage.
Contact us today to learn more about our services and how we help clients stay safe in this complex security environment.
Talk to us about how Velosio can help you realize business value faster with end-to-end solutions and cloud services.
"*" indicates required fields