Top Tips to Tackle IT Crisis Preparation and Employee Training
Mastering IT Crisis Preparation. Discover essential plans, training, and security measures to safeguard your business.
Mastering IT Crisis Preparation. Discover essential plans, training, and security measures to safeguard your business.
We all like to be “glass half full” people, but let’s face it, in a post-COVID world, we realize that disaster happens—either man-made or natural. How can your IT department ensure its prepared for anything?
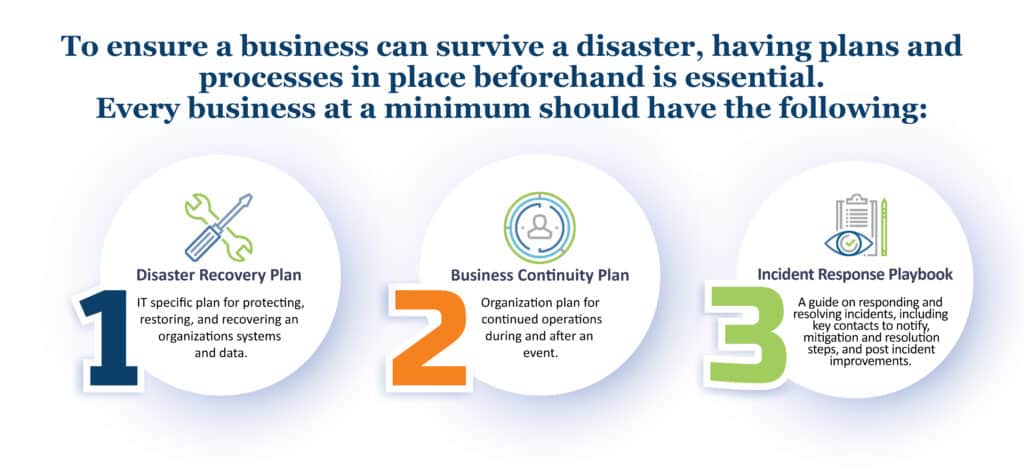
To prepare an IT department for a natural or human-related crisis, you must think about your business from every possible angle. To do that, you need to work with other key stake holders to understand how they do business and what systems and data drive their productivity. You also need to understand the possible events that can impact your business and estimate their likelihood of occurring. Understanding the scope of what you’re protecting and what you’re protecting it from is not static and should be reviewed at least annually. To ensure a business can survive a disaster, having plans and processes in place beforehand is essential.
While technology plays an important role in crisis response, it’s only one part of a comprehensive strategy, says Sean O’Brien, cybersecurity lecturer and Yale Law School Fellow. “Effective crisis preparation requires a holistic approach that takes into account the needs of all stakeholders, including employees, customers, and the broader community,” he states.
Preparing for a crisis starts with creating a detailed plan that outlines the necessary steps to take in case of an emergency. This plan should also include protocols for backing up and recovering data, ensuring network security, communicating with stakeholders, and ensuring the safety of employees. According to O’Brien, the founder of the Yale Law School Privacy Lab. “Every organization should conduct regular drills and simulations to test the effectiveness of their plan.”
Having a plan is important, but testing and constantly improving that plan is essential for it to be effective in a real-world situation. Testing shows how comprehensive the plan is and highlights areas for improvements (Was anything missed? What could have been done better? Easier? Faster?). Testing also allows for those that are taking the actions to practice. A well tested plan will reduce downtime and could minimize the impact of an incident.
From a security perspective the best course of action is to shift toward zero-trust architecture ASAP. Zero trust reinforces the idea that there is no safe haven, no castle to lock away your data. With its three principles (verify explicitly, use least privileged access, and assume breach), zero trust provides a road map for a more secure organization while preparing them to scale safely and be more prepared as cyberthreats evolve. By assuming breach, our goal is to decrease the impact.
Crisis planning is typically led by the head of an organization’s IT department but buy in from key stake holders is important because they will help drive the importance of security, planning and help identify what systems, data, and processes are most important.
No matter who is leading, it is important to have specific strategies in place to address different types of emergencies. Dealing with a volcano eruption or a hurricane will require different actions compared to handling a cyber attack. While it may not be possible to plan for every situation, it is crucial to have plans that are customized for specific crisis scenarios. These plans should clearly outline the necessary steps to effectively respond to the emergency.
Every employee should be well trained and prepared for crisis aversion. Your employees can either pose a significant threat or serve as a strong defense against cyber-attacks. Inadequately trained staff members have the potential to weaken even the most advanced security measures. All it takes is one individual downloading a corrupted file or clicking on a harmful link, and cybercriminals can easily infiltrate your systems. The good news is that equipping your team with fundamental cybersecurity skills is a highly effective and simple method to safeguard your business against cyber threats. Annual security training should be a minimum, recurring attack simulations, and consistent messaging from all levels of management of its importance. It is critical that employees have a clear process for reporting and responding to cyber incidents.
Initially, your goal is to demonstrate to employees how individual actions are directly linked to protecting the organization and its customers from cyberthreats. Reassure employees that it’s ok to raise their hand when they think they did something wrong, or something feels off. Remind them consistently that mistakes happen, but a small mistake can become larger if you pretend like nothing happened. Inform employees about current dangers such as ransomware as a service, recent security breaches, and vulnerabilities that could lead to business interruptions.
Provide training to help employees recognize phishing emails, texts, social media messages, apps, and websites. Simple actions like checking for grammar errors, the use of formal greetings (e.g. Dear Sir/Madam), and verifying sender email addresses (e.g. bankofamerica@gmail.com) or hovering over links before clicking can help prevent potential crises. The rise of remote-hybrid work has heightened the risk of cyber threats, with malicious actors targeting unsecured personal devices, Remote Desktop and VPN weaknesses, and even USB devices. It is crucial to focus training efforts on ensuring that employees understand the risks associated with their devices and how to protect themselves.
Remote-hybrid work has increased the threat of cyberthreats—with more threat actors capitalizing on unsecured personal devices, Remote Desktop and VPN vulnerabilities, and things like USB devices. It’s important that your training efforts focus on ensuring that employees are aware of the risks that come with their devices and what they can do to stay safe.
Crisis response plans will be informed by your business model, strategy, and the regulations that dictate how these things are accomplished within your industry. But, all industries need to clearly define and document your game plan, communicate it to key employees, and run routine tests to ensure that you’re ready to fend off threats of all types, whether it’s natural disaster or driven by malicious actors.
It’s worth noting that cyber incidents come in many different “flavors,” and you’ll want to consider those nuances as you develop a response plan. Like, how will you:
The biggest mistake that an IT department can make is not backing up their data securely. If a client has been breached, the very first thing we ask them is if they have their data backed up. It can mean the difference between a dead-in-the-water or business-as-usual scenario. In addition to ransomware attacks, you need a backup in case of system crashes, storage failures, theft, or simply human error. A company’s data is its life blood.
In the event of a disaster, getting your business up and running again quickly can give you a competitive advantage. Many businesses around the world have suffered huge losses and reputation damage after poorly handling incidents. Being able to assure your customers and partners that you have a regularly tested disaster recovery and business continuity plan can make your business more reliable than those that don’t. Proper planning means your doors can stay open or open back up faster in the face of a disaster.
Every crisis plan requires continuous maintenance. A neglected plan, one that falls out of date by failing to address new and evolving threats—as well as changes within the organization itself—is ultimately worthless. If you need help with IT crisis preparation, reach out to an expert at Velosio today!
Talk to us about how Velosio can help you realize business value faster with end-to-end solutions and cloud services.
"*" indicates required fields